There are many good open source NAC solutions available, but some of the most popular include:
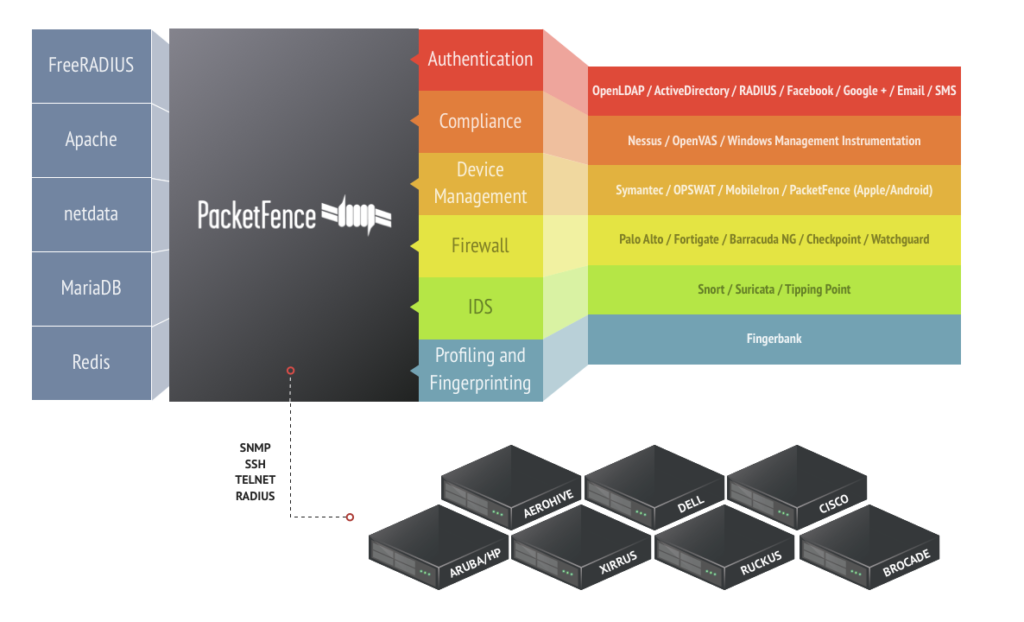
- PacketFence: PacketFence is a comprehensive NAC solution that offers a wide range of features, including endpoint compliance checking, vulnerability scanning, and remediation, as well as role-based access control and guest network management. It is easy to deploy and manage, and it is compatible with a wide range of network devices.

- openNAC: openNAC is another popular open source NAC solution that offers a similar set of features to PacketFence. It is also easy to deploy and manage, and it is compatible with a wide range of network devices.
- FreeNAC: FreeNAC is a more lightweight open source NAC solution that is ideal for small businesses and home networks. It offers a basic set of features, such as endpoint compliance checking and role-based access control.
Opens in a new windows3msecurity.com
FreeNAC open source NAC logo
- ClearPass OSS: ClearPass OSS is an open source version of the ClearPass NAC solution from Aruba Networks. It offers a wide range of features, including endpoint compliance checking, vulnerability scanning, and remediation, as well as role-based access control and guest network management. It is more complex to deploy and manage than some of the other open source NAC solutions, but it offers a lot of flexibility and scalability.
The best open source NAC solution for you will depend on your specific needs and requirements. If you need a comprehensive NAC solution with a wide range of features, then PacketFence or openNAC are good options. If you are looking for a more lightweight solution for a small business or home network, then FreeNAC may be a better choice. And if you need a solution that is compatible with Aruba Networks devices, then ClearPass OSS is a good option.
Here is a table comparing the four open source NAC solutions mentioned above:
Feature | PacketFence | openNAC | FreeNAC | ClearPass OSS |
Endpoint compliance checking | Yes | Yes | Yes | Yes |
Vulnerability scanning | Yes | Yes | No | Yes |
Remediation | Yes | Yes | No | Yes |
Role-based access control | Yes | Yes | Yes | Yes |
Guest network management | Yes | Yes | No | Yes |
Ease of deployment | Easy | Easy | Easy | Complex |
Ease of management | Easy | Easy | Easy | Complex |
Compatibility | Wide range of devices | Wide range of devices | Limited devices | Aruba Networks devices |
Ultimately, the best way to decide which open source NAC solution is right for you is to evaluate your specific needs and requirements and then try out a few different solutions to see which one you like best.
Here are the steps on how to configure PacketFence:
- Install PacketFence on a server or virtual machine with at least 16 GB of RAM and 200 GB of disk space.
- Configure the PacketFence database.
- Configure the PacketFence web interface.
- Configure the PacketFence network devices.
- Configure the PacketFence authentication sources.
- Configure the PacketFence policies.
Here are the detailed steps for each of these tasks:
- Install PacketFence
You can download the PacketFence installation package from the PacketFence website. Once you have downloaded the package, you can install it using the following steps:
- Open a terminal window and navigate to the directory where you downloaded the PacketFence installation package.
- Run the following command to install PacketFence:
sudo dpkg -i packetfence-<version>.deb
Replace <version> with the version of PacketFence that you downloaded.
- Once the installation is complete, you can start the PacketFence service by running the following command:
sudo service packetfence start
- Configure the PacketFence database
PacketFence uses a MySQL database to store its configuration and data. You will need to create a new MySQL database and user for PacketFence.
- Log in to your MySQL server.
- Create a new database called packetfence.
- Create a new user called packetfence with a password of your choice.
- Grant the packetfence user full privileges on the packetfence database.
- Configure the PacketFence web interface
The PacketFence web interface is used to manage PacketFence. You will need to configure the web interface to use the MySQL database that you created in the previous step.
- Open the /etc/packetfence/packetfence.conf file in a text editor.
- Find the section that starts with # Web interface configuration.
- Uncomment the following lines:
database_type = mysql
database_host = localhost
database_name = packetfence
database_user = packetfence
database_password = <password>
Replace <password> with the password that you chose for the packetfence user in the previous step. 4. Save the file and exit the text editor.
- Configure the PacketFence network devices
PacketFence needs to be configured on your network devices in order to enforce its policies. The specific configuration steps will vary depending on the type of network devices that you are using.
For example, if you are using Cisco switches, you will need to configure the following:
- The switchport mode to be dot1x or macauth.
- The switchport authentication method to be radius.
- The RADIUS server IP address to be the IP address of the PacketFence server.
- The RADIUS server secret to be the shared secret that you configured in PacketFence.
- Configure the PacketFence authentication sources
PacketFence can authenticate users against a variety of authentication sources, such as Active Directory, LDAP, and RADIUS. You will need to configure the authentication sources that you want to use in PacketFence.
For example, if you want to use Active Directory, you will need to configure the following:
- The Active Directory domain name.
- The Active Directory username and password of a user with administrative privileges.
- Configure the PacketFence policies
PacketFence policies define how users are authenticated and authorized to access the network. You will need to configure the policies that you want to use in PacketFence.
For example, you could create a policy that allows all users to access the network, but only allows users in the administrators group to access the management interface.
Once you have configured PacketFence, you can start using it to enforce your network security policies.