Network infrastructure is the foundation of any digitized establishment. Therefore, risks associated with these network systems cannot be overstated. A new malicious botnet has emerged, known as the KV-Botnet, notable for its stealthy maneuvers and its specific focus on Cisco, DrayTek, and Fortinet devices. This article highlights the intricate workings of this destructive botnet.
Understanding the Stealthy KV-Botnet
Botnets are not an uncommon occurrence in the digital landscape; they have been part of the architecture of cyber threats for years. What sets the KV-Botnet apart is its stealth and precision.
The Silent Menace
The KV-Botnet remains remarkably invisible in its initial stages of infection. It sneaks its way into the network system, laying in wait as it builds its strength. The botnet is silent but deadly, often leaving no noticeable traces of its existence until it’s too late.
“The KV-Botnet, a silent dread laying in wait, is the modern symbol of stealthy cyber threats.”
The Focused Attack
This malicious bot primarily targets Cisco, DrayTek, and Fortinet devices, three leading players in the networking equipment industry. By infiltrating these commonly used devices, the KV-Botnet can spread exponentially, causing wide-spread devastation.
Technical Aspects of the KV-Botnet
Understanding the technical specifications of the KV-Botnet is integral to recognizing its destructive potential.
Infection and Proliferation
The KV-Botnet leverages different stages of infection, each elaborating on its stealth and proliferation.
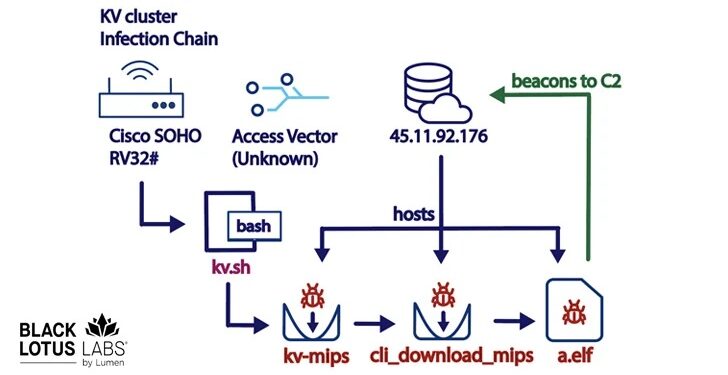
Initial compromise: The botnet first compromises the device through various methods, including exploiting known vulnerabilities or weak security measures.
Second-stage payload: Once inside the system, the KV-Botnet deploys its second phase, containing malicious codes necessary for the botnet’s functionality.
Attack Vector
The primary attack vector of the KV-Botnet is well known devices from Cisco, DrayTek, and Fortinet. By focusing on these devices, the botnet can ensure a higher success rate due to their extensive use in various industries.
Read more about the technical aspects of botnets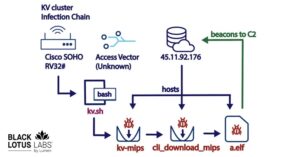
Implications for Businesses and End Users
The presence of the KV-Botnet sets a new precedent for the types of cyber threats businesses and end-users might face.
Compromised security
Once the KV-Botnet fully infiltrates a device, it can manipulate the systems, compromise data, and even conduct DDoS attacks.
Widespread risk
Given the broad usage of Cisco, DrayTek, and Fortinet devices, the range of this threat is vast, encompassing numerous sectors, including healthcare, finance, and governmental institutions.
Preparation and Mitigation
It’s not a question of ‘if’, but ‘when’ your network will fall under cyber threats like the KV-Botnet. Here are some crucial steps to prepare and mitigate these stealthy attacks.
Update security measures: Regularly update device firmware and apply security patches to minimize the attack surface.
Use complex and unique credentials: Reduce the risk of a breach by avoiding default login credentials.
Stay informed: Keep up to date with the latest security news to be aware of new threats.
Wrapping Up
The KV-Botnet’s stealthy nature and focused approach make it a formidable cyber threat. By understanding its strategies and preparing accordingly, businesses and end-users can significantly reduce their risk. Remember, the primary countermeasure to such cyber threats lies within the realm of proactive and dynamic cybersecurity protocols.
“In the face of silent threats like the KV-Botnet, being vigilant and proactive is the best defense.”