The Vital Security Audit or How to Discover Network Security Weakpoints
1. What is a Network Security Audit
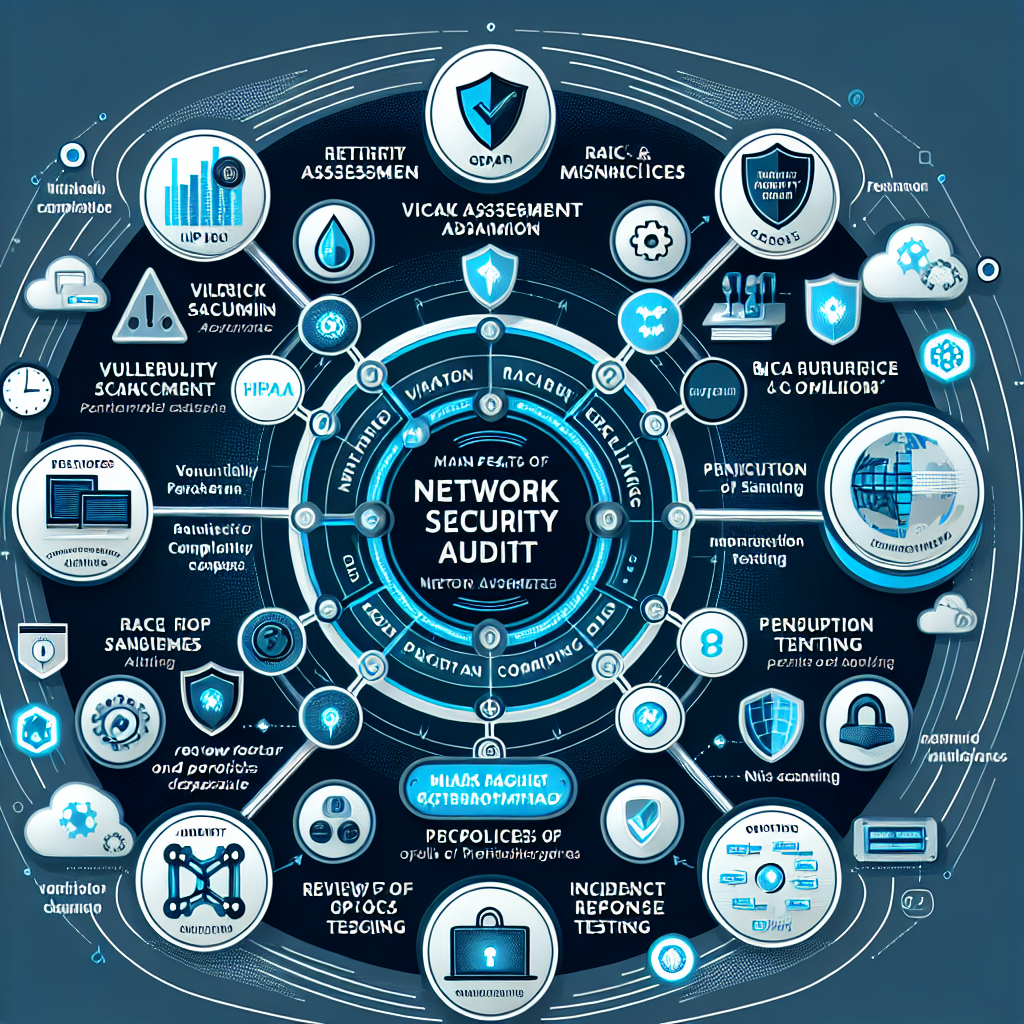
Network security audits are essential in securing and protecting an organization’s network infrastructure. The audits encompass checking the overall network, devices and infrastructure, and even the management protocols, in order to determine the threats and vulnerabilities and understand the potential hazards to security. A network security audit has several key goals:
- Vulnerability Assessment: The process of identifying and evaluating security weaknesses in a network which might be exploited by malicious attackers.
- Risk Mitigation: Plan and recommend security measures to combat security risks and protect sensitive data.
- Compliance Assurance: Provide industry specific regulations and compliance standards as well as enforce organizational security policies in the network.
- Optimization: Finding ways to make security measures more efficient and effective.
2. Benefits of Regular Audits
Some reasons why organizations kept network security audits on a regular schedule were:
- Maintain Network Security – Audits help an organization to protect itself from evolving network security threats by identifying and bidding it adieu before it becomes a risk.
- Ensuring Data Security – Audits protect your sensitive data from unauthorized access or theft, and in turn maintain the trust of customers and stakeholders.
- Regulatory Compliance: Audits ensure that you are compliant to the regulatory laws that are industry specific and thus ensure reduced legal and financial risks.
- Business Continuity – Audits help organizations to bolter their defences and decrease vulnerabilities which decrease the chances of downtime brought on by a security incident.
3. PJ Networks’ Audit Process
PJ Networks conduct audits comprised by the following steps:
- Risk Assessment: Identify threat and vulnerabilities by assessing how data is stored, industry regulations and your organization’s risk profile.
- Vulnerability Scanning: Using automated tools to scan the network for known vulnerabilities, misconfigurations, and possible points of entry that may be targeted by attackers.
- Penetration Testing: Penetration testing includes a controlled and simulated cyber attack aiming to locate and target security weaknesses in your system.
- Policy and Procedure Review: Assess current security policies and procedures to ensure the organization follows best practices and standards.
- Incident Response Testing: Testing the ability of the organization to respond to security incidents efficiently.
4. Compliance and Regulations
Types of network security audits as per industry and government regulations:
- GDPR (General Data Protection Regulation)
- HIPAA: Health Insurance Portability and Accountability Act
- PCI DSS: Payment Card Industry Data Security Standard
- NIST 800-171: National Institute of Standards and Technology Special Publication 800-171
By making regular network security audits, organizations can facilitate compliance with these regulations and reduce legal and financial risks.






