Introduction
In today’s rapidly evolving technological landscape, securing your network has become more critical than ever before. Network Access Control (NAC) is a comprehensive solution that ensures only authorized devices and users gain access to your network resources. This article will guide you through the concept of NAC, its importance, and how to install it, along with a hands-on demonstration upon request.
Table of Contents
Understanding Network Access Control (NAC)
- Defining NAC and its Purpose
- Why NAC is Crucial in Modern Networks
Key Benefits of Network Access Control
- Ensuring Network Security
- Managing Bring Your Own Device (BYOD) Policies
- Simplifying Compliance
Components of Network Access Control
- Authentication and Authorization
- Endpoint Security
- Policy Enforcement
Installing Network Access Control
- Preparing for NAC Implementation
- Step-by-Step Installation Guide
- Configuration and Customization
NAC Deployment Best Practices
- Assessing Your Network’s Needs
- Involving Stakeholders
- Regular Updates and Monitoring
NAC Demonstration on Request
- Hands-On Experience with NAC
- Understanding User Experience
- Real-world Benefits Showcased
Common Challenges and Solutions
- Compatibility Issues with Legacy Systems
- Addressing Connectivity Concerns
- User Education and Training
Future Trends in Network Access Control
- Integration with Artificial Intelligence
- Zero Trust Security Model
Understanding Network Access Control (NAC)
Defining NAC and its Purpose
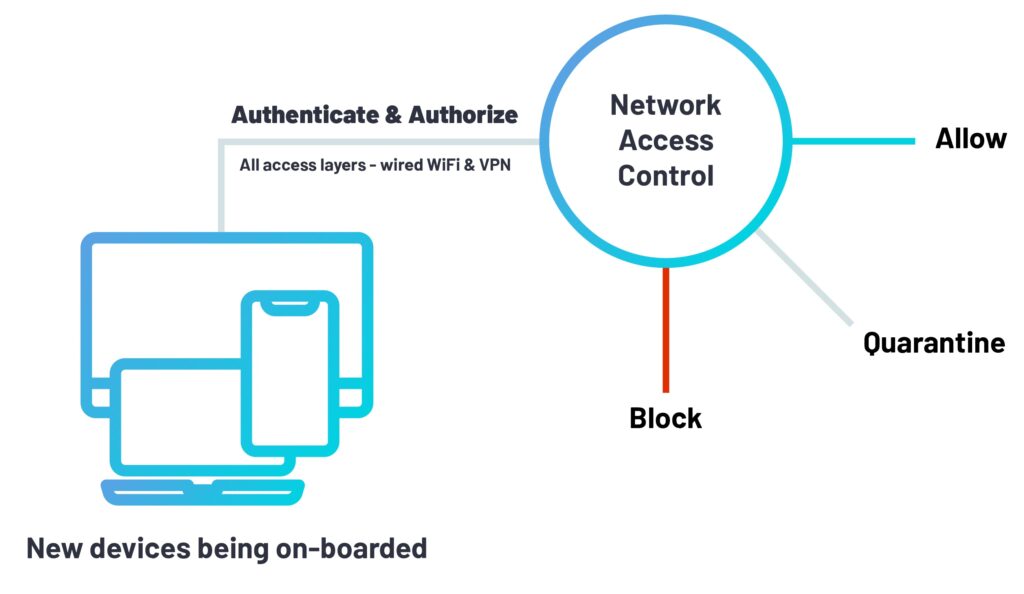
Network Access Control (NAC) refers to a security solution that manages and enforces access policies for devices and users attempting to connect to a network. Its primary purpose is to ensure that only authorized entities can access network resources while maintaining the security and integrity of the network infrastructure.
Why NAC is Crucial in Modern Networks
In today’s interconnected environment, the traditional perimeter-based security approach is no longer sufficient. With the rise of remote work and the Internet of Things (IoT), networks are more vulnerable to breaches. NAC addresses these challenges by providing granular control over who can access the network, preventing unauthorized access and potential security breaches.
Key Benefits of Network Access Control
Ensuring Network Security
NAC plays a pivotal role in maintaining network security by enforcing security policies and identifying potential threats. It helps in preventing unauthorized devices from joining the network, safeguarding sensitive data from malicious actors.
Managing Bring Your Own Device (BYOD) Policies
Many organizations allow employees to use their personal devices for work, which can increase security risks. NAC enables organizations to implement strong security measures for personal devices, ensuring they meet the necessary security standards before connecting to the network.
Simplifying Compliance
Regulatory compliance is a major concern for businesses across various industries. NAC helps in enforcing compliance by ensuring that devices connecting to the network adhere to the required security standards and policies.
Components of Network Access Control
Authentication and Authorization
Authentication verifies the identity of users and devices attempting to access the network, while authorization determines the level of access they are granted. NAC ensures that only authenticated and authorized entities can enter the network.
Endpoint Security
Endpoints are often entry points for cyberattacks. NAC ensures that endpoints are secure and compliant with security policies before allowing access to the network.
Policy Enforcement
NAC enforces network policies based on predefined rules. These policies can include granting or denying access, segregating network segments, and applying security protocols.
Installing Network Access Control
Preparing for NAC Implementation
Before installing NAC, conduct a thorough assessment of your network infrastructure, including devices, users, and existing security measures. This will help in designing appropriate access policies.
Step-by-Step Installation Guide
- Choose the Right NAC Solution: Select a NAC solution that aligns with your organization’s needs and requirements.
- Install NAC Server: Set up the NAC server in your network environment.
- Configure Policies: Define access policies based on user roles, device types, and security levels.
- Integrate with Network Devices: Integrate NAC with switches, routers, and access points for enforcement.
Configuration and Customization
Customize NAC settings according to your organization’s security policies. This includes defining rules for different user groups, setting up guest network access, and configuring threat detection mechanisms.
NAC Deployment Best Practices
Assessing Your Network’s Needs
Before deploying NAC, conduct a thorough assessment of your network’s requirements, considering factors such as network size, user mobility, and types of devices.
Involving Stakeholders
NAC deployment should involve various stakeholders, including IT teams, security personnel, and end-users. Their insights and cooperation are crucial for a successful implementation.
Regular Updates and Monitoring
NAC systems should be regularly updated with the latest security patches and configurations. Additionally, continuous monitoring ensures that any anomalies or security breaches are promptly addressed.
NAC Demonstration on Request
Would you like to see the power of NAC in action? Request a demonstration, and we’ll provide you with a hands-on experience. Witness how NAC enhances network security and simplifies access management.
Hands-On Experience with NAC
During the demonstration, we’ll simulate various scenarios, showcasing how NAC identifies and blocks unauthorized devices, grants access to legitimate users, and ensures compliance.
Understanding User Experience
The NAC demonstration will also highlight the user experience, demonstrating how seamless and secure the process of connecting to the network can be with NAC in place.
Contacting Us for a Demo
To request a demonstration of NAC, please reach out to us via email at sanjay@pjnetworks.com or give us a call at +91 9818361787. We’re excited to show you the benefits of NAC firsthand.
Common Challenges and Solutions
Compatibility Issues with Legacy Systems
Integrating NAC with legacy systems can pose compatibility challenges. However, with proper planning and possibly some system updates, these challenges can be overcome.
Addressing Connectivity Concerns
In some cases, users might face connectivity issues due to NAC policies. Proper communication and user education about the benefits of NAC can help alleviate such concerns.
User Education and Training
Educating users about NAC and its benefits is essential. Regular training sessions can empower users to adhere to security protocols and understand the significance of NAC.
Future Trends in Network Access Control
Integration with Artificial Intelligence
The integration of AI in NAC systems enhances threat detection and response capabilities. AI algorithms can analyze network behavior in real-time, identifying anomalies and potential breaches.
Zero Trust Security Model
NAC aligns with the Zero Trust security model, which assumes that no one, whether inside or outside the network, should be trusted by default. NAC’s granular access control embodies this principle.
Conclusion
Network Access Control is a fundamental tool for modern network security. By ensuring only authorized users and devices access your network resources, NAC mitigates security risks and enhances compliance. Through this article, you’ve gained insights into NAC’s benefits, components, installation process, best practices, and its future in network security. Request a demonstration to experience NAC in action and take a proactive step toward safeguarding your network.
FAQs (Frequently Asked Questions)
What is Network Access Control (NAC)? Network Access Control (NAC) is a security solution that manages and enforces access policies for devices and users connecting to a network.
Why is NAC important? NAC is crucial as it prevents unauthorized access to the network, enhances security, manages BYOD policies, and ensures compliance.
How does NAC enhance network security? NAC enforces security policies, authenticates users and devices, and identifies potential threats before granting network access.
Can NAC be integrated with existing network infrastructure? Yes, NAC can be integrated with existing network devices such as switches, routers, and access points for policy enforcement.
What is the future of NAC? The future of NAC involves integration with AI for advanced threat detection and alignment with the Zero Trust security model.