How to Configure SIEM: A Complete Guide to Successful Implementation
Implementing a Security Information and Event Management (SIEM) solution is crucial for organizations to effectively monitor and analyze their network security. However, the process of setting up and configuring a SIEM can be complex and requires careful planning. In this comprehensive guide, we will walk you through the steps to configure and implement a SIEM solution successfully. From understanding the importance of SIEM to selecting the right technology and optimizing its performance, we will cover everything you need to know to ensure the success of your SIEM deployment.
Table of Contents
- Understanding the Importance of SIEM
- Assessing Your Organization’s Needs
- Selecting the Right SIEM Technology
- Configuring the Basic Settings for SIEM Integration
- Identifying and Configuring Data Sources
- Tuning Your SIEM Solution
- Customizing Event Data Sent to the SIEM Server
- Integrating External Data Sources
- Automating SIEM Processes
- Maintaining and Updating Your SIEM Solution
1. Understanding the Importance of SIEM
A SIEM solution plays a crucial role in an organization’s cybersecurity infrastructure. It collects and processes logs from various sources, providing valuable insights to detect and respond to security incidents effectively. By centralizing log collection and analysis, a SIEM solution enables security teams to identify suspicious behavior, potential threats, and compliance issues. It acts as a force multiplier for security analysts, helping them prioritize their efforts and respond to incidents promptly.
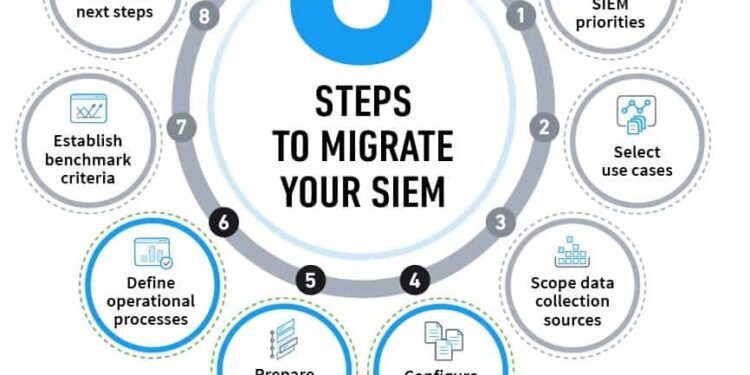
2. Assessing Your Organization’s Needs
Before implementing a SIEM solution, it is essential to assess your organization’s specific requirements. Consider factors such as the size of your network, the volume of log data generated, compliance regulations, and the level of threat detection needed. Conducting a thorough evaluation will help you determine the scope of SIEM integration and define the key objectives for your deployment.
3. Selecting the Right SIEM Technology
Choosing the right SIEM technology is critical for the success of your implementation. Evaluate different SIEM solutions based on factors such as scalability, performance, ease of use, integration capabilities, and vendor reputation. Consider whether an on-premise, cloud-based, or hybrid deployment model suits your organization’s needs. Additionally, ensure that the SIEM solution aligns with your compliance requirements and supports integration with other security tools in your environment.
4. Configuring the Basic Settings for SIEM Integration
Once you have selected a SIEM solution, it is time to configure the basic settings for SIEM integration. This includes setting up the connection to the SIEM server, specifying the protocol (TCP or UDP), and defining the main and mirror syslog server connection settings. You can choose to send events to a remote syslog server via the syslog protocol and decide whether to remove local copies of events after they are sent to the SIEM server. Consider the events format (structured data or JSON) that best suits your SIEM server’s recognition capabilities.
5. Identifying and Configuring Data Sources
To make the most of your SIEM solution, it is crucial to identify and configure the appropriate data sources. Create an inventory of your assets and understand your systems to determine what data needs to be captured for security analysis and monitoring. Ensure that your SIEM solution collects logs from all relevant sources, including firewalls, critical systems, applications, and network devices. Fine-tune the audit policies and filters to collect only the necessary log data, reducing storage costs and minimizing false positives.
6. Tuning Your SIEM Solution
To optimize the effectiveness of your SIEM solution, it is essential to fine-tune its configuration based on your organization’s unique needs. Assign criticality levels to systems and assets, prioritizing alerts and events accordingly. Regularly review and update correlation rules to keep up with evolving threat patterns. Customize the event data sent to the SIEM server, focusing on the most relevant information for analysis. Leverage external data sources, such as threat intelligence feeds, to enhance threat detection capabilities.
7. Customizing Event Data Sent to the SIEM Server
Customizing the event data sent to the SIEM server allows you to tailor the information to your organization’s specific requirements. You can choose to send events by asset, policy, or both, depending on your analysis needs. Specify whether to send events for in-compliance or out-of-compliance results, based on risk scores or compliance thresholds. Fine-tune these settings to ensure that your SIEM solution generates actionable intelligence and provides meaningful insights for threat detection and incident response.
8. Integrating External Data Sources
While a SIEM solution excels at collecting and analyzing internal data, integrating external data sources can further enhance its capabilities. Subscribe to threat intelligence feeds that provide indicators of compromise (IoCs) and other relevant information about potential threats. Leverage APIs and services that offer insights into file reputation, IP addresses, or domain reputation. Integrating these external data sources into your SIEM solution enables analysts to have a more comprehensive view of the threat landscape and make better-informed decisions during investigations.
9. Automating SIEM Processes
Automation plays a crucial role in maximizing the efficiency and effectiveness of your SIEM solution. Implement automation processes for tasks such as log collection, analysis, and response. Automate the classification and ranking of alerts to ensure analysts prioritize critical incidents. Regularly update log correlation rules and maintain firewall configurations to stay current with emerging threats. Leverage machine learning and artificial intelligence capabilities to detect anomalies and identify potential threats in real-time. Automating these processes allows security teams to focus on more complex tasks and respond to incidents swiftly.
10. Maintaining and Updating Your SIEM Solution
Maintaining and updating your SIEM solution is vital to its long-term effectiveness. Stay current with software updates and patches to ensure the solution’s stability and security. Regularly review and fine-tune your SIEM configuration based on changes in your network environment, compliance requirements, and emerging threats. Conduct periodic audits and assessments to identify any gaps or areas of improvement. Back up your SIEM databases regularly to prevent data loss and maintain the integrity of your log archives.
In conclusion, the successful implementation of a SIEM solution requires careful planning, configuration, and ongoing maintenance. By understanding the importance of SIEM, assessing your organization’s needs, selecting the right technology, and configuring the necessary settings, you can optimize the effectiveness of your SIEM deployment. Regular tuning, customization, and automation will ensure that your SIEM solution remains robust and capable of detecting and responding to security incidents effectively. Stay proactive by integrating external data sources, keeping your SIEM solution up to date, and continuously improving its configuration to stay ahead of emerging threats.